International Journal of Applied Mathematics and Informatics
E-ISSN: 2074-1278
Volume 8, 2014
Notice: As of 2014 and for the forthcoming years, the publication frequency/periodicity of NAUN Journals is adapted to the 'continuously updated' model. What this means is that instead of being separated into issues, new papers will be added on a continuous basis, allowing a more regular flow and shorter publication times. The papers will appear in reverse order, therefore the most recent one will be on top.
Submit a paper | Submission terms | Paper format
Volume 8, 2014
Title of the Paper: Laminar and Turbulent Simulations of Several TVD Schemes in Two-Dimensions – Part II
Authors: Edisson S. G. Maciel
Pages: 102-116
Abstract: This work, second of this study, describes four numerical tools to perform perfect gas simulations of the laminar and turbulent viscous flow in two-dimensions. The Yee, Warming and Harten, Yee and Kutler, Yee, Warming and Harten and Yee schemes are implemented to accomplish the numerical simulations. The Navier-Stokes equations, on a finite volume context and employing structured spatial discretization, are applied to solve the supersonic flow along a ramp in two-dimensions. Three turbulence models are applied to close the system, namely: Cebeci and Smith, Baldwin and Lomax and Sparlat and Allmaras. All schemes are TVD (“Total Variation Diminishing”) ones, where the Yee, Warming and Harten, Yee and Kutler, and Yee, Warming and Harten are derived from a first order upwind scheme and the Yee is derived from a first order symmetrical scheme. The latter reaches TVD properties by the appropriated definition of a limited dissipation function that uses non-linear limiters. The convergence process is accelerated to the steady state condition through a spatially variable time step procedure, which has proved effective gains in terms of computational acceleration (see Maciel). The results have shown that the Yee and Kutler and Yee schemes yield the best results in terms of the prediction of the shock angle at the ramp. Moreover, the wall pressure distribution is also better predicted by the Yee algorithm.
Title of the Paper: Influence of Irradiation on Mechanical Properties of PMMA
Authors: P. Kratky, D. Manas, M. Manas, M. Stanek, M. Ovsik, V. Senkerik, J. Navratil
Pages: 93-101
Abstract: The goal of the experimental study is clarify the effect of modification of the surface layer by irradiation on the mechanical properties of the PMMA tested using the instrumented nanohardness test. Surface layer was affected by radiation cross-linking technology which allows polymer materials modification followed by the change of their end-use properties. Compared to the heat and chemical-heat treatment of metal materials (e.g. hardening, nitridation, case hardening), cross-linking in polymers affects the surfaces in micro layers. These mechanical changes of the surface layer are observed in the instrumented nanohardness test. The subject of this research is the influence of irradiation dosage on the changes of mechanical properties of PMMA.
Title of the Paper: Compact City Model Analysis for a Metropolitan Area using GIS Relationship between Population and Land Use
Authors: Manrique Ruiz, Luis Carlos, Yamamoto Kayoko
Pages: 82-92
Abstract: This study aims to evaluate a compact city model by considering the relationship between different types of land use and population. Urbanization promotion areas in Aomori, Sendai and Sapporo metropolitan areas were studied. All areas are implementing the compact city model in the northern part of Japan; however, they correspond to small, middle and large scale sizes respectively. In this study GIS is used to manipulate the geographical data. The main results of this study are: (1) The compact city model was validated using a residual Kriging model and a compactness index using land use transformation and population density data. (2) There is a commuter belt in both the Sendai and Sapporo Metropolitan areas as shown by population density according to the residual Kriging model. (3) The compactness index was useful in validating the compact city model in the different metropolitan areas, and also in contrasting the model implementation in different time periods. (4) Although Sendai and Sapporo promote residential areas, it is necessary to improve the mixed use of land and commuter belt areas in order to incrementally increase the index of compactness.
Title of the Paper: The Role of Millionshschkov's Zero-Fourth Cumulant Hypothesis in Homogenous Isotropic Turbulence
Authors: Christos Mamaloukas, Amitabha Chanda, Himandri Pai Mazumdar
Pages: 77-81
Abstract: In this paper a new model of one-point, one-time fourth cumulant of homogeneous and isotropic turbulence in wavenumber space is suggested. The fourth cumulant in this model varies in wavenumber. In the final period decay it is identically zero, in compliance with the zero-fourth cumulant hypothesis, proposed by Millionshchikov. But as wavenumber goes to lower values the fourth cumulant becomes non-zero. The suggested model is based on a near-Gaussian distribution, built with the help of Gaussian distribution and truncated Hermite polynomial.
Title of the Paper: A Study on the Improvement of the Information Security System Evaluation & Certification in Korea
Authors: Gyeong-Eun Seo, Tae-Sung Kim
Pages: 68-76
Abstract: In 1993, six countries (U.S., UK, France, Germany, Canada, the Netherlands) developed CC (Common Criteria). Through a combination of rating of CC evaluation results, it can be mutually acceptable and presented to establish the future direction of the technical evaluation. Korea, in 2006, registered to CCRA certificate authorities and has issued certification on a wide ranges information security products. However, evaluation system work based CC is done at limited agencies such as IT product development security companies, rating agencies. For this reason, relevant papers in the country and the CC certification system for the study of the problems and the lack of improvement. So, this study derived influencing factors to again acquiring CC certification from information security companies that have received CC certification at least once since CC certification was introduced in Korea. The five variables were derived such as motivation of certification, the need for certification, discomfort of CC certification, satisfaction of certification, decision on re-certification. Based on them, exploratory model was designed and verified. By checking satisfaction and complaints about CC, find improvements.
Title of the Paper: Coding over Elliptic Curves in the Ring of Characteristic Two
Authors: Abdelhamid Tadmori, Abdelhakim Chillali, M’hammed Ziane
Pages: 65-67
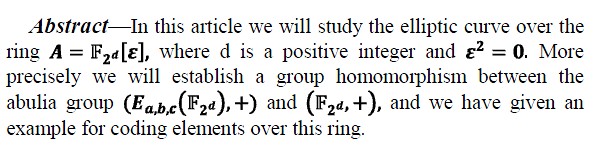
Title of the Paper: Generalized Lagrangians for the Lagrange Problem with Equality Constraints
Authors: Javier F. Rosenblueth
Pages: 54-64
Abstract: In this paper we deal with necessary and sufficient conditions for the Lagrange problem in the calculus of variations involving equality constraints. The approach we follow is based on adding a penalty term to the standard Lagrangian. This type of augmentability has been successfully applied to constrained minimum problems in finite dimensional spaces, particularly in the development of computational procedures, and the main purpose of this paper is to generalize this approach by introducing the notions of weak and strong augmentability which yield first and second order necessary conditions for local minima in the calculus of variations. Moreover, we provide also a simple proof to show that the standard sufficient conditions for a weak local minimum imply weak augmentability.
Title of the Paper: The Derivatives of Trigonometric Functions
Authors: Chii-Huei Yu
Pages: 50-53
Abstract: This article uses the mathematical software Maple for the auxiliary tool to study the differential problem of some type of trigonometric functions. We can obtain the closed forms of any order derivatives of this type of functions by using binomial theorem. On the other hand, we propose two examples to do calculation practically. The research methods adopted in this study involved finding solutions through manual calculations and verifying our answers by using Maple.
Title of the Paper: The Impact of Personal Information Breaches on the Firm‘s Value in the South Korean Stock Market – A Comparative Study of IT and Non-IT Industries
Authors: Seol Kim, Seokbae Sohn, Seokha Koh
Pages: 42-49
Abstract: As the collection of customers’ personal information is becoming economically feasible, security breaches are also increasing. Therefore, it is important to estimate the direct and indirect costs of personal information security breaches. In this study, we examined the effects of personal information security breaches on the market values of breached firms and analyzed the difference between IT and non-IT industries. This study was formulated and conducted by using the event study methodology. We investigated the effects of personal information breaches on the firm’s value in Korea stock market. The study result shows that information security breaches have an effect on firm’s value from the day before breaches occurred. We also found that the magnitude of effect is different between IT and Non-IT Industries. We aim to provide an investment standard of information security to corporate decision makers and help to calculate the costs of personal information breaches in the stock market.
Title of the Paper: Properties of the Cost Matrix and the P-Median Problem
Authors: Marta Janackova, Alzbeta Szendreyova
Pages: 34-41
Abstract: This contribution deals with the p-median problem and with the properties of the distribution network.We study the dependence of the computational time of exact method for p-median problem on characteristics of underlying transportation network. The research is motivated by previous experiences in experimental work with approximate method for the p-median problem. Networks obtained from the internet were used in mentioned experiment. The networkswere notgiven by their graphical structure, but by the cost matrix. During these experiments it was found that the distribution of the distance values may considerable influence the effectiveness of the solving process, which is based on the branch and bound method. We want to verify the similar hypothesis for the specific algorithm developed for the p-median problem. We also solve a problem of the network deformation. We check up changing of the computational time of the p-median problem after rounding the values of the cost matrix. We found out what differences are between the solutions before and after deformation of the network. We are interested in the impact of the deformation on the computational time, on the availability of the service, on the objective values and on the changing of the service centers locations as well.
Title of the Paper: Transportation Problem and Related Tasks with Application in Agriculture
Authors: Miloš Šeda, Jan Roupec, Jindřiška Šedová
Pages: 26-33
Abstract: In this paper, we deal with well-known distribution problems and discuss their restrictions, extensions and modifications including a possible application in agriculture. We show that the transportation problem can be transformed to an allocation, location and set covering problem using special constraints, but because of NP-hardness of the last problem it needs quite different methods of its solving. Another modification of the transportation problem, the crop problem, has an application in agriculture, but we must deal with uncertain data. We propose a genetic algorithm and fuzzy logic approach for solving these problems
Title of the Paper: New Solutions of the Heat Equation
Authors: Jacob M. Manale
Pages: 15-25
Abstract: Using a Lie symmetry group generator and a generalised form of Euler’s formula for solving second order ordinary differential equations, we determine new symmetries for the heat equation, leading to new solutions. As an application, we test a formula resulting from this approach on thin plate heat conduction.
Title of the Paper: Radial Approach to the Emergency Public Service System Design with Generalized System Utility
Authors: Jaroslav Janáček
Pages: 7-14
Abstract: The paper is focused on methods of the public service system design, where the generalized utility is considered instead the usual disutility represented by distance. On the contrary to the former formulations, the generalized utility defined for a public service system assumes that user’s utility comes generally from more than one located service center and the individual contributions from relevant centers are weighted by reduction coefficients depending on a center order. Real instances of the public service system design problem are characterized by a big number of possible facility locations. The classical approaches to the related problems make use of location-allocation model. Complexity of location-allocation problems considerably grows with the number of possible locations and so commercial IP-solvers often fail due to enormous computational time or extreme memory demands. This drawback can be overcome by the approximate covering approach based on so called radial model of the problem. Within this paper, we suggest radial formulation of the public service system design with the generalized utility and compare the approaches used location-allocation model with those, which are based on the radial formulation
Title of the Paper: A Note on Generalized Hermite Polynomials
Authors: Clemente Cesarano
Pages: 1-6
Abstract: By starting from the general theory of the one-variable Hermite polynomials, we will introduce a bi-dimensional generalization of them that is useful to obtain a different approach with the harmonic oscillator functions. We will see some interesting properties of this class of Hermite polynomials and we also discuss the related applications on the particular partial differential equations.



